Critical Vulnerabilities Found and Fixed by Cybersecurity Researcher Deepak Kumar on SSC Website
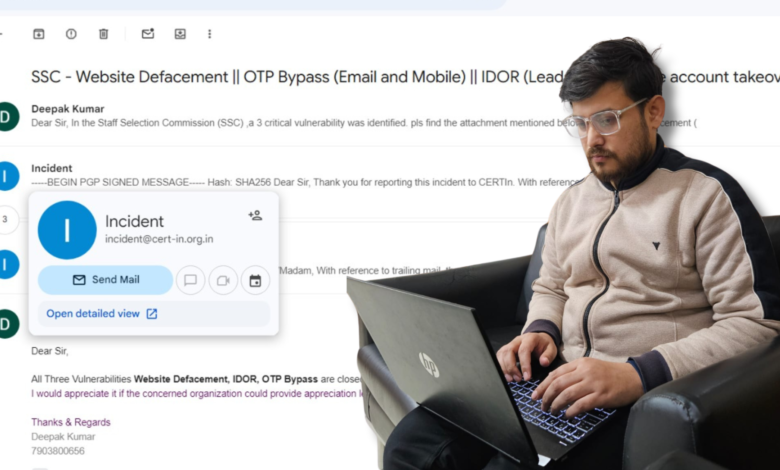
Deepak Kumar, a renowned cybersecurity researcher, recently uncovered three critical vulnerabilities on the Staff Selection Commission (SSC) website, posing significant risks to user data and system integrity. His responsible disclosure to the Indian Computer Emergency Response Team (CERT-In) led to swift action, and the vulnerabilities have now been resolved (Incident ID: CERTIn-22175824).
Details of the Vulnerabilities
1. Website Defacement
This vulnerability allowed attackers to modify the website’s content and create fake pages. Such attacks could mislead users and lead to phishing attempts, exposing sensitive information.

2. IDOR in “Forgot Password” Feature
A flaw in the “forgot password” functionality leaked answers to security questions of SSC candidates. This breach could have allowed attackers to compromise user accounts.
3. OTP Bypass
Weaknesses in the OTP verification system enabled attackers to bypass email and mobile OTP checks, granting unauthorized access to user accounts.
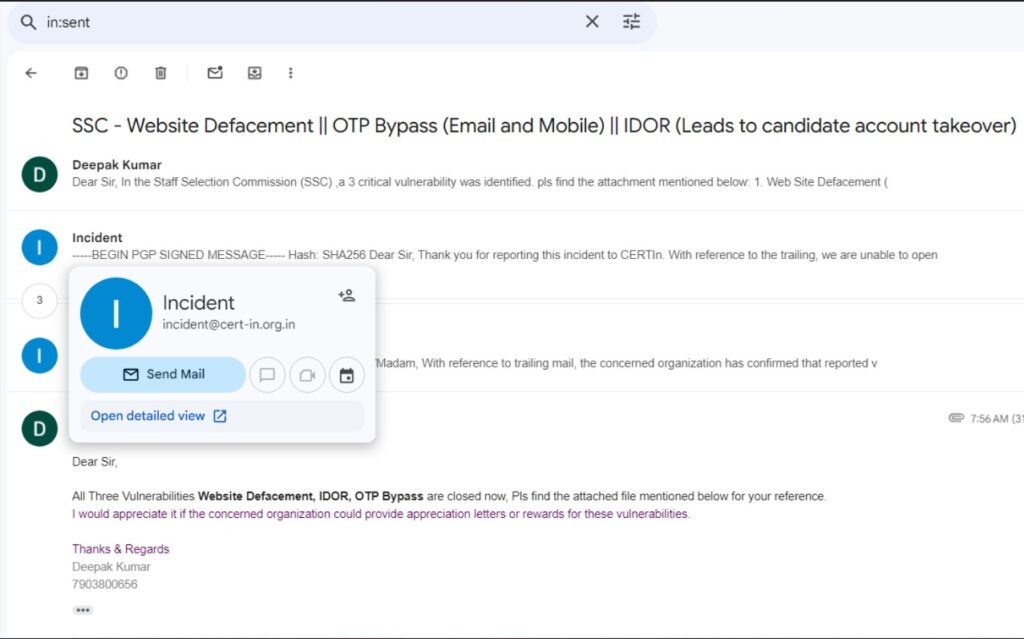
CERT-In’s Response
Upon reporting these vulnerabilities, CERT-In worked closely with SSC to address the flaws. The issues were fixed promptly, ensuring the safety and integrity of user data. CERT-In acknowledged Deepak’s efforts in strengthening cybersecurity, emphasizing the importance of responsible disclosure in safeguarding public systems.
Deepak Kumar’s Contributions
Deepak Kumar, based in Dumraon, Bihar, has a track record of identifying vulnerabilities in high-profile systems, including those of RBI, IRCTC, the Election Commission of India, LIC, and UPSC. His proactive approach and collaboration with CERT-In have played a crucial role in securing sensitive government platforms.
Public Awareness
This incident highlights the importance of regular security audits and robust defenses against cyberattacks. Users are advised to:
Use strong passwords and change them regularly.
Enable two-factor authentication wherever possible.
Be cautious about sharing sensitive information online.





